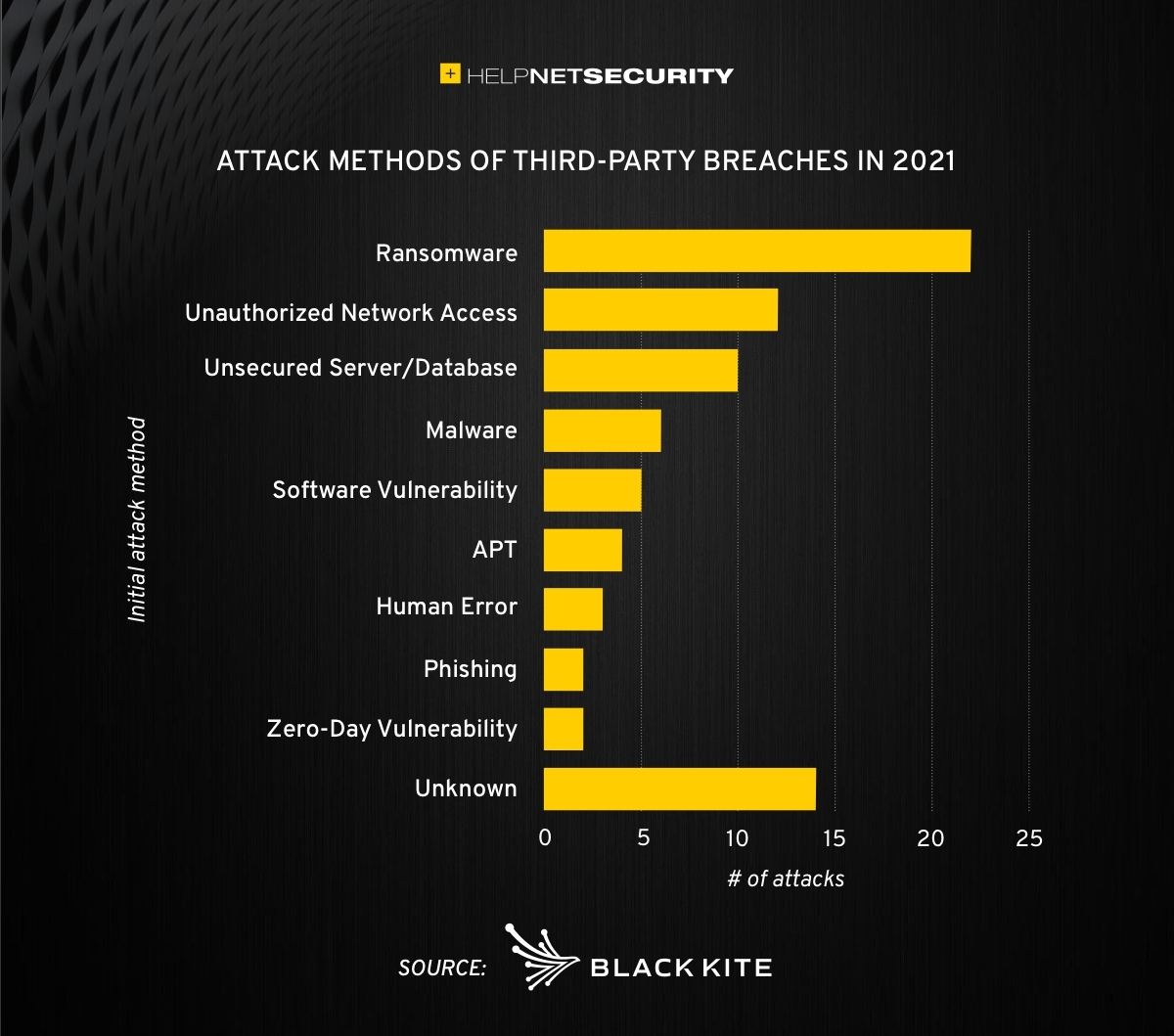
The Evolving Third-Party Data Breach Landscape: What's Going On and How to Protect Your Data With Vendor Risk Management Software - CENTRL

Only two percent of IT experts consider third-party secure access a top priority - Help Net Security

In the wake of a data breach, what are three important steps to avoid a repeat and establish long-term data security? - Wavestone